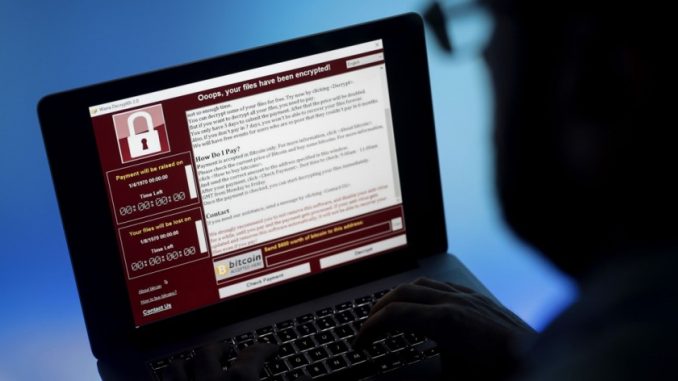
The recent incidents of Computers getting locked worldwide due to a Ransomware named WannaCry have brought tears in the eyes of many users. We need to know a few facts about the Ransomware and its effects. Read On :
Ransomware is a malware that locks your computer making it inaccessible. It encrypts your data and then demands you to pay a ransom for unlocking the computer or decrypting the data.
Let us take a look at the file encrypting ransomware called WannaCry – the biggest ransomware attack in history!
1. What is WannaCry and why has it become a global phenomenon?
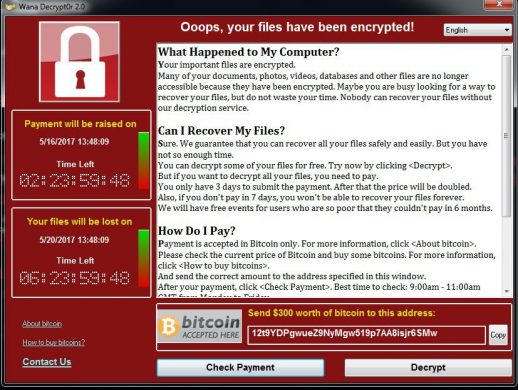
The WannaCry Ransomware attack begun on Friday 12th May 2017 and within a day it managed to infect over 200,000 computers in 150 countries making it the biggest ransomware attack in history. This malware encrypts the victim’s files, then demands a ransom of $300 in bitcoins. If the ransom is not paid within 3 days, the price doubles to $600. And if the ransom is not paid within 7 days, the malware threatens to delete all the encrypted data permanently.
2. How and from where did WannaCry come ?
The U.S. National Security Agency (NSA) discovered an underlying vulnerability (MS17-010) in Microsoft’s Server Message Block (SMB) protocol. This protocol is used by Windows machines to communicate with file systems over a network. The NSA acted over-wise and chose not to inform Microsoft about this vulnerability. It instead tried to take advantage of the situation and built an exploit called EternalBlue which could be used for gathering sensitive data which could be used by NSA.
Shadow Broker – hacking group, stole the details of this exploit and leaked them in public which ultimately led to trigger the WannaCry outbreak worldwide.
Interestingly, Microsoft had already released a security update to patch this vulnerability in March 2017, but who cares? Many users and organizations ignored or failed to apply this update, exposing their systems to the attack.
3. Did WannaCry spread through emails?
Initially, it was thought so. But, the latest reports stated that the attackers behind this malware targeted systems running vulnerable SMB ports (SMB v1, in this case). When these systems were traced, the leaked EternalBlue exploit was used to launch the attack.
4. What makes WannaCry so scary?
The WannaCry ransomware is a self-propagating worm. This means, after it infects one computer, it searches for other computers in the network with the same vulnerability. If found, it can spread on its own without any user action.
5. Is the WannaCry attack over?
No. While the attack that occurred on 12th May 2017 was slowed down by a security researcher, it hasn’t stopped and is still active on the Internet. What’s even worse, some newer variants of this ransomware have been detected in the wild. The chances of a second wave of attack are really high.
6. How to stay protected against WannaCry?
- First and foremost, install any and all available security updates immediately on your computer – specifically the update for MS17-010
- Disable Server Message Block version 1 (SMBv1). You can seek help from experts to do this. If you want to do it yourself, follow the steps listed below:
- Go to Control Panel > Programs > Features
- Click Turn Windows Features on and off
- Scroll down to find SMB 1.0/CIFS File Sharing Support and uncheck
- Click OK and restart the computer
- Keep your antivirus software updated and ensure you are using the latest version.
- Always keep a secure backup of your important data
- Beware of emails that ask you to enable ‘macros’ to view the content
- This incident should be a glaring reminder for us to keep our OS and software up-to-date. Ensure that your computer’s Automatic Updates are enabled
- Do not click on links or download attachments received in unwanted or unexpected emails




Leave a Reply